Prepare certificate for using on Endpoint Manager and Tigase server
Please use the machine where the certificate is installed.
Right click on Start, choose Run, type mmc.exe and hit Enter
From Console Root – click on File and then on Add/Remove Snapin…
Select the Certificates from the list and click on Add
If you are not sure if the certificate is under the user or computer account, you can add them both.
Click ok to load the interface.
Locate the certificate that you want to use, usually present under the Personal – Certificates
folder
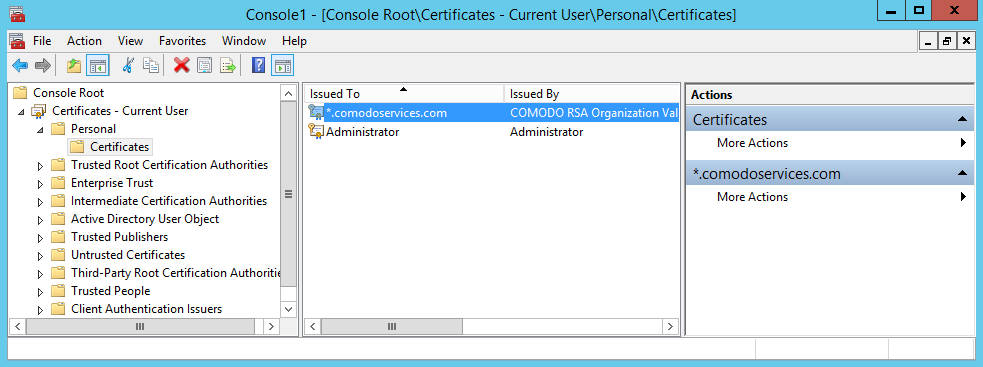
To view more information about the certificate, please double click the name to open the certificate information.
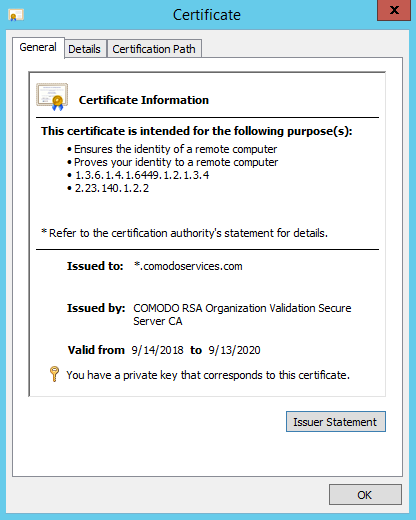
From the General tab we can see that the certificate has the private key associated with it and is able to validate anything.comodoservices.com but will not be able to validate comodoservices.com
To confirm we can go to the Details tab Subject Alternative Name section
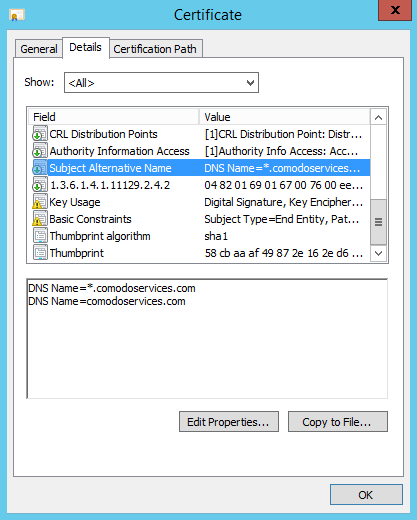
In this section we can see two entries.
The first entry will validate anything.comodoservices.com and the second entry will validate the main
domain comodoservices.com.
If you are using a multidomain certificate, in this section you will be able to see all the FQDN’s/IP’s
that the certificate is able to cover.
In our case this wildcard certificate will suit our needs.
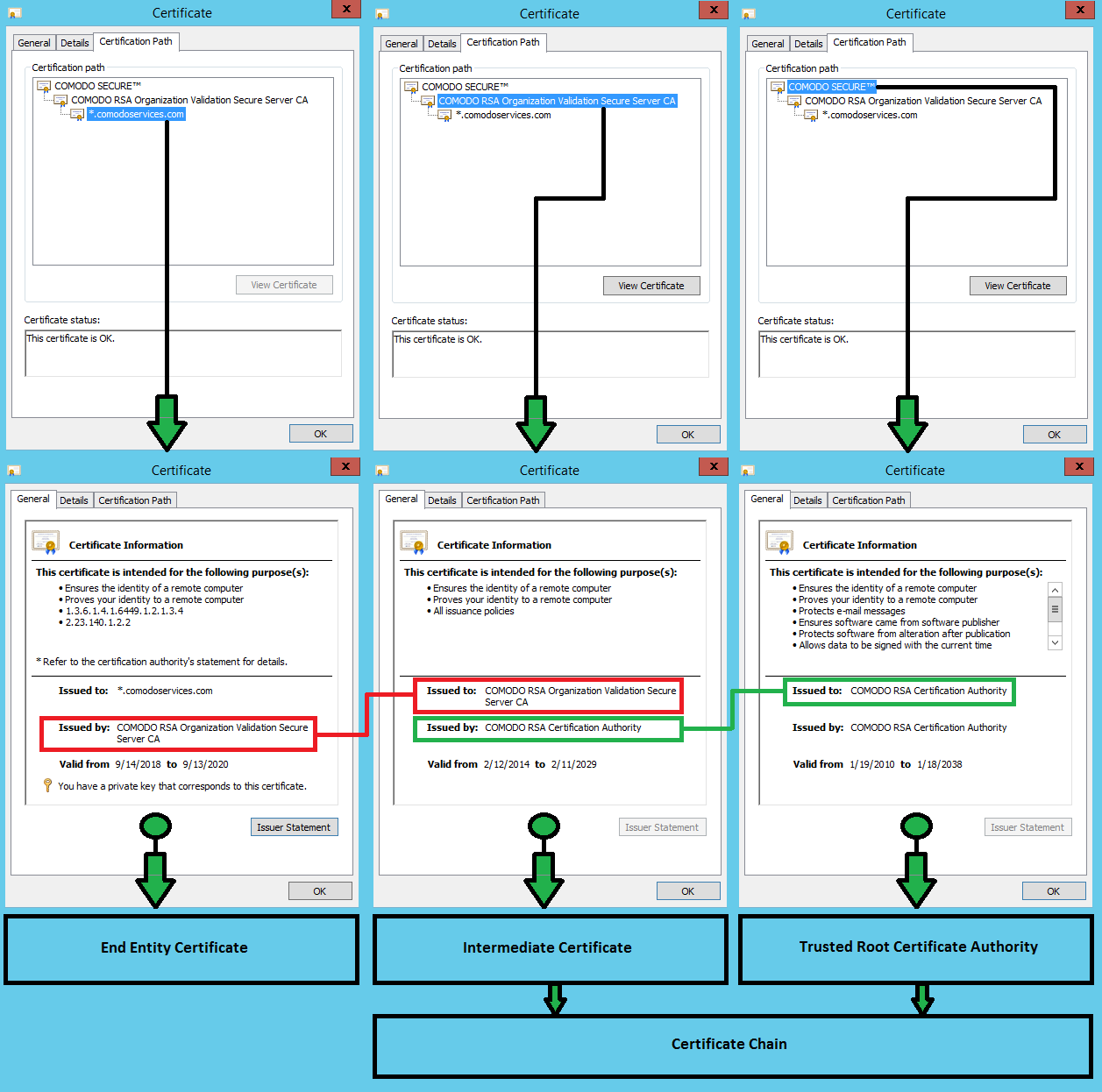
From the Certificate Path tab, we can view the certificate chain and confirm that the certificate – End
Entity Certificate is able to link to a trusted root certificate using one or two intermediate
certificates.
Please review the bellow print screen.
(In this case we have only one intermediate certificate)
From the Certificates windows, right click on the certificate name – All Tasks – Export…
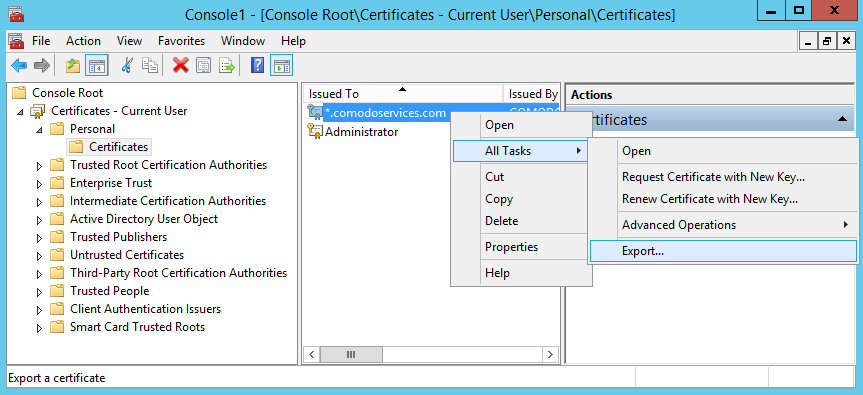
Click Next
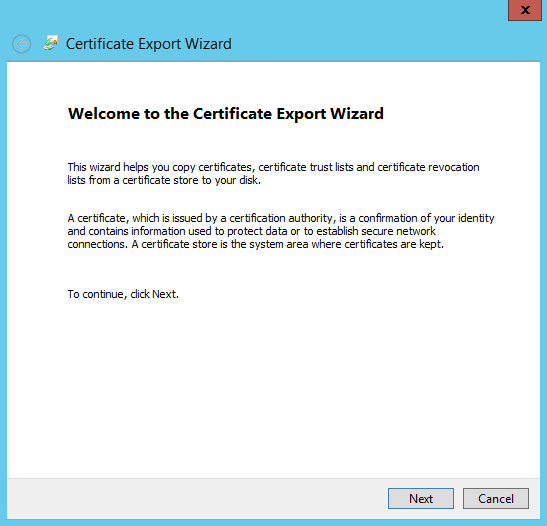
Please choose “Yes, export the private key” and click Next
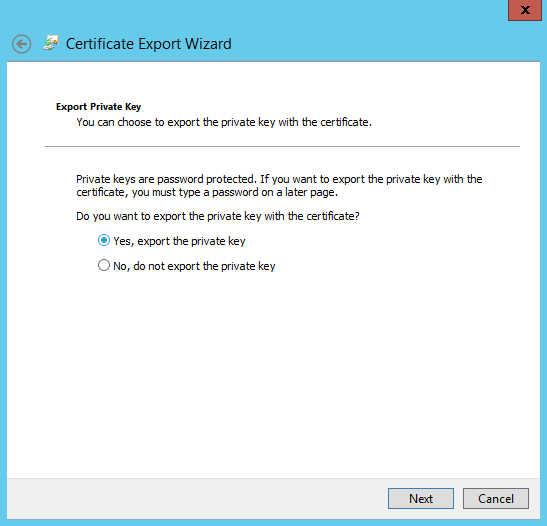
Please choose “Include all certificates in the certification path if possible” and click Next This option will include the certificate chain.
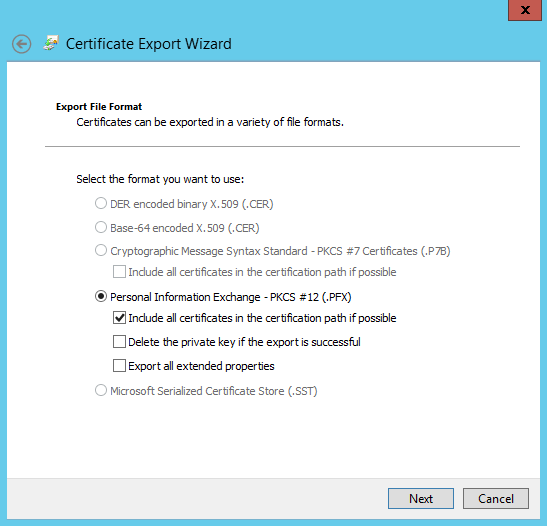
Provide a password and click Next
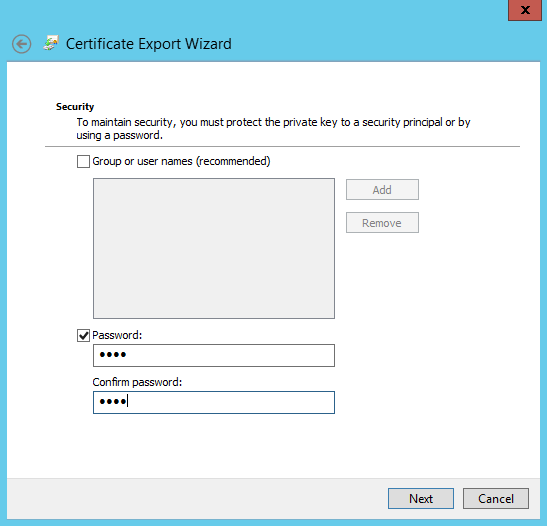
Please provide a name, choose where to save it and click Next
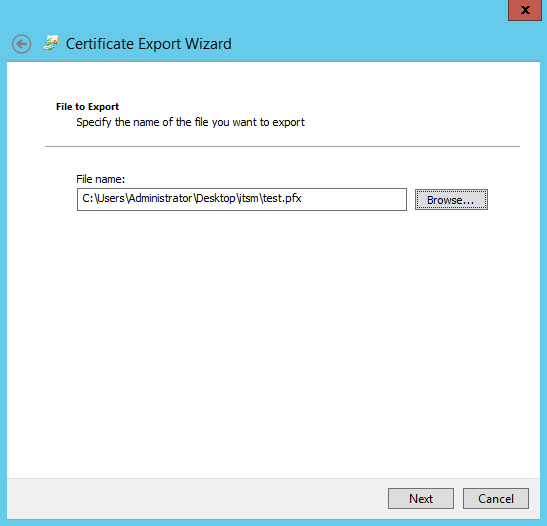
The last step is to click on Finish to export the certificate to a .pfx file
You have 2 options available to extract the certificates that you will be using on Endpoint Manager (ITSM) server and Tigase server:
- Option 1: Use the script scriptpfx.sh to create cert.crt, cert.key and in this case comodoservices.com.pem
- Option 2: Manually create cert.crt, cert.key and comodoservices.com.pem from a .pfx file
Create a folder on the itsm or tigase server using for example FileZilla.
Copy the .pfx file to the folder.
Create file scriptpfx.sh in the created folder (near .pfx file) with following content:
#!/bin/bash
openssl pkcs12 -in $1 -nocerts -nodes -passin pass:$2 | sed -ne '/-BEGIN PRIVATE KEY-/,/-END PRIVATE KEY-/p' > clientcert.key
openssl pkcs12 -in $1 -clcerts -nokeys -passin pass:$2 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > clientcert.crt
openssl pkcs12 -in $1 -cacerts -nokeys -chain -passin pass:$2 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > cacerts.crt
a="$(openssl crl2pkcs7 -nocrl -certfile cacerts.crt | openssl pkcs7 -print_certs -text -noout | sed -n 's/^.*CN=//p' | sed -n 1p)"
b="$(openssl crl2pkcs7 -nocrl -certfile cacerts.crt | openssl pkcs7 -print_certs -text -noout | sed -n 's/^.*CN=//p' | sed -n 2p)"
if [ "$a" == "$b" ]; then
cabundle="$(cat cacerts.crt | wc -l)"
if [ "$cabundle" -gt 1 ]; then
cat cacerts.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > rootca.crt
cat cacerts.crt > intermediatefile.crt
nr="$(cat rootca.crt | wc -l)"
sed -i 1,"${nr}"d intermediatefile.crt
cat rootca.crt > newcertificatechain.crt
cabundle1="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate1.crt
cat intermediate1.crt >> newcertificatechain.crt
nr1="$(cat intermediate1.crt | wc -l)"
sed -i 1,"${nr1}"d intermediatefile.crt
cabundle2="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate2.crt
cat intermediate2.crt intermediate1.crt rootca.crt > newcertificatechain.crt
rm intermediate2.crt
rm intermediate1.crt
rm rootca.crt
rm intermediatefile.crt
else
cat intermediate1.crt rootca.crt > newcertificatechain.crt
rm intermediate1.crt
rm rootca.crt
rm intermediatefile.crt
fi
else
cat rootca.crt > newcertificatechain.crt
rm rootca.crt
rm intermediatefile.crt
fi
cat clientcert.key > cert.key
cat clientcert.crt newcertificatechain.crt > cert.crt
cat clientcert.key clientcert.crt newcertificatechain.crt > $3
rm clientcert.key
rm clientcert.crt
rm cacerts.crt
rm newcertificatechain.crt
else
echo The certificate chain is not included in the $1.
echo Please create again the $1 and include the certificate chain.
fi
else
cat clientcert.key > cert.key
cat clientcert.crt newcertificatechain.crt > cert.crt
cat clientcert.key clientcert.crt cacerts.crt > $3
rm clientcert.key
rm clientcert.crt
rm cacerts.crt
fi
- Run
chmod +x scriptpfxtest.shto make the file executable - Run
./scriptpfxtest.sh test.pfx 1234 comodoservices.com.pemto generate cert.crt, cert.key and comodoservices.com.pem
Format to use the command:
./scriptpfxtest.sh Parameter1 Parameter2 Parameter3
Where:- Parameter1: test.pfx – is the name of the .pfx file
- Parameter2: 1234 – is the password for the .pfx file
- Parameter3: comodoservices.com.pem – is the FQDN.pem that you want to use
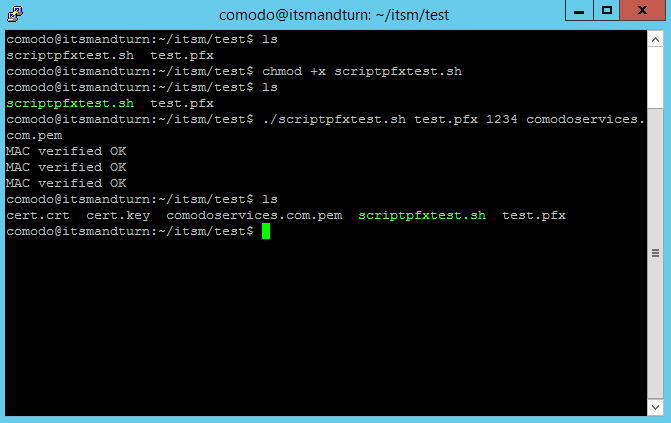
The script execution will create:
- cert.key
- cert.crt
- comodoservices.com.pem
To confirm that the files are generated correctly you can use the following commands:
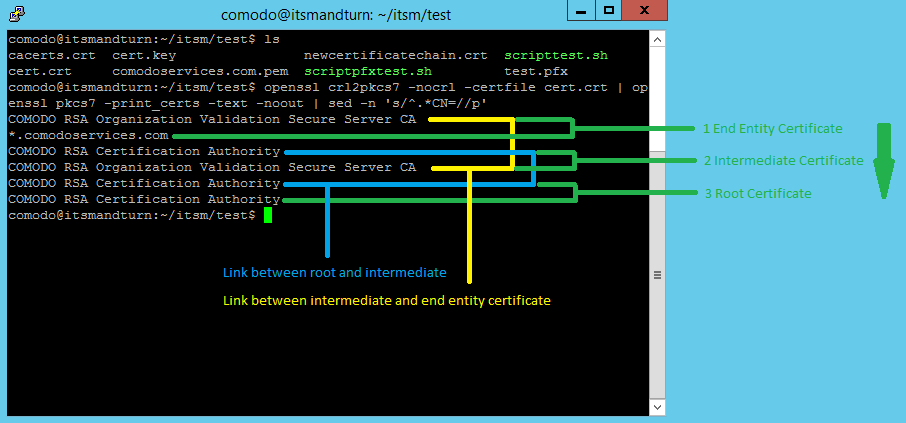
openssl crl2pkcs7 -nocrl -certfile cert.crt | openssl pkcs7 -print_certs -text -noout | sed -n
's/^.*CN=//p'
This will confirm if the certificate chain is in the correct order from top to bottom.
You can use the same command on the tigase certificate.(Example: comodoservices.com.pem)
The difference between Endpoint Manager (ITSM) certificate and tigase certificate is that the tigase
certificate will have on top the private key.
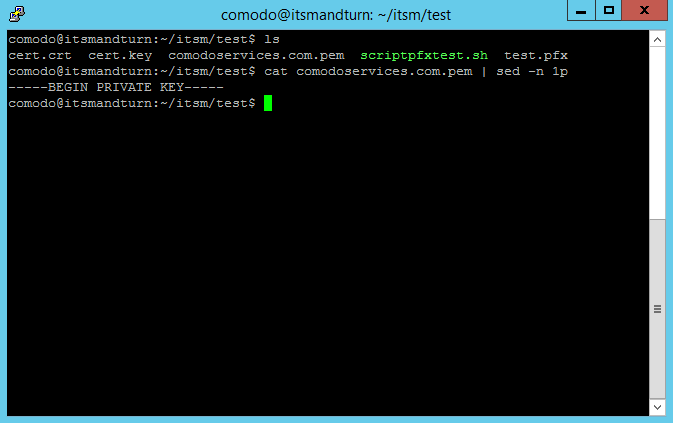
To verify this, we can use the following command:
cat comodoservices.com.pem | sed -n 1p
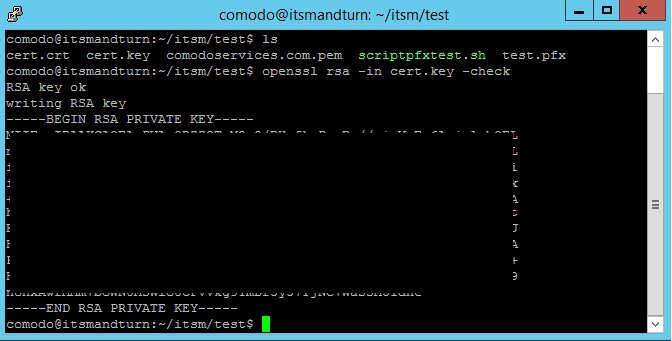
We can verify the private key using this command:
openssl rsa -in cert.key -check
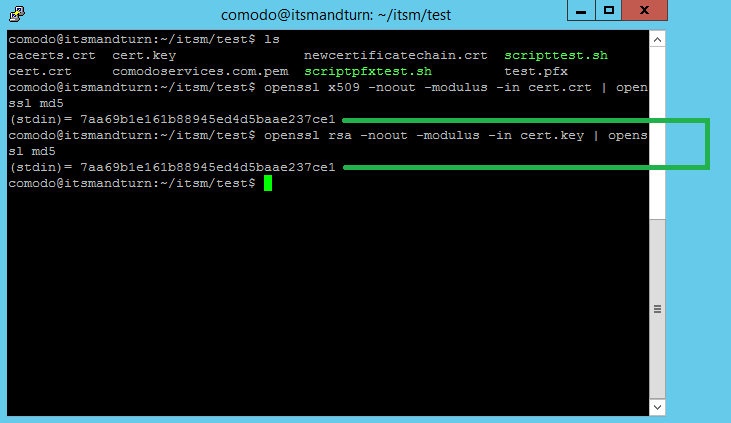
To confirm that the private key is associated with the certificate we can use the following command:
openssl x509 -noout -modulus -in cert.crt | openssl md5
openssl rsa -noout -modulus -in cert.key | openssl md5
By receiving the same number, we confirm that private key is associated with the certificate
Copy the .pfx file on a folder on Endpoint Manager (ITSM) or Tigase server using for example FileZilla
To create cert.key please run this command:
openssl pkcs12 -in test.pfx -nocerts -nodes |
sed -ne '/-BEGIN PRIVATE KEY-/,/-END PRIVATE KEY-/p' > cert.key
To extract only the certificate run this command:
openssl pkcs12 -in test.pfx -clcerts -nokeys |
sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > clientcert.crt
To extract the certificate chain, use this command:
openssl pkcs12 -in test.pfx -cacerts -nokeys -chain |
sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > cacerts.crt
To confirm that the cacerts.crt has the correct order, please run this command:
openssl crl2pkcs7 -nocrl -certfile cacerts.crt |
openssl pkcs7 -print_certs -text -noout | sed -n 's/^.*CN=//p'
If the certificate chain is as order, bottom to top instead of top to bottom
you can use script to reverse the order
Create file scriptorder.sh (in the folder near .pfx file) with following content:
#!/bin/bash
cabundle="$(cat $1 | wc -l)"
if [ "$cabundle" -gt 1 ]; then
cat $1 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > rootca.crt
cat $1 > intermediatefile.crt
nr="$(cat rootca.crt | wc -l)"
sed -i 1,"${nr}"d intermediatefile.crt
cat rootca.crt > newcertificatechain.crt
cabundle1="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate1.crt
cat intermediate1.crt >> newcertificatechain.crt
nr1="$(cat intermediate1.crt | wc -l)"
sed -i 1,"${nr1}"d intermediatefile.crt
cabundle2="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate2.crt
cat intermediate2.crt intermediate1.crt rootca.crt > newcertificatechain.crt
rm intermediate2.crt
rm intermediate1.crt
rm rootca.crt
rm intermediatefile.crt
else
cat intermediate1.crt rootca.crt > newcertificatechain.crt
rm intermediate1.crt
rm rootca.crt
rm intermediatefile.crt
fi
else
cat rootca.crt > newcertificatechain.crt
rm rootca.crt
rm intermediatefile.crt
fi
else
echo The file is empty.
echo Lines = $cabundle
fi
- Run the script. To make the script executable use this command:
chmod +x scriptorder.sh - Once the script is executable, we can run it providing the cacerts.crt as parameter:
./scriptorder.sh cacerts.crt
See Example below.
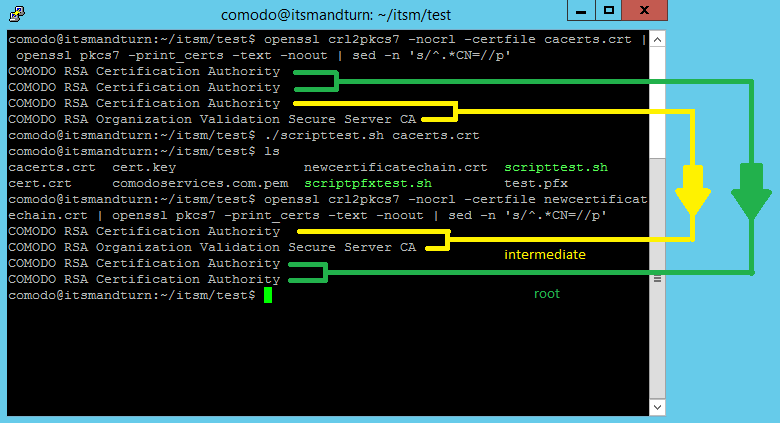
If you don’t want to use the script, you can use the following commands to extract the certificates in order:
-
This command will extract the first certificate from the file, in our case the root:
cat cacerts.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > rootca.crt -
The second command will delete the certificate from the cacerts.crt to be able to extract the second
certificate available
nr="$(cat rootca.crt | wc -l)";sed -i 1,"${nr}"d cacerts.crt
You can use these three commands to extract your certificate chain and after that you can use
cat to concatenate them in the correct order.
Example to create comodoservices.com.pem:
cat cert.key clientcert.crt intermediate.crt root.crt > comodoservices.com.pem
Example to create cert.crt:
cat clientcert.crt intermediate.crt root.crt > cert.crt
To confirm that the certificate files have been created/extracted correctly, you can use the options from Option 1 to verify them.